Traefik, Docker and your vps part 1
I have an "amazing" website here www.themwebs.me it's fast simple and cheaply hosted with a yearly fixed cost on a VPS with www.hostinger.com.
I wanted a space where I could play with stuff, containers, apis, test tools, test web frameworks, backend and frontend.
Specifically: I needed a place to host backend APIs that I might create like this one made with with python using Flask.
I have these apps running:
Now if playing with servers is not your jam, stop reading and head over to your favourite backend as service or serverless platforms those are great too I use them often.
knowledge about docker is assumed. I will be focusing on Traefik and configuring it more than docker basics.
Ready?
Let's go.
What
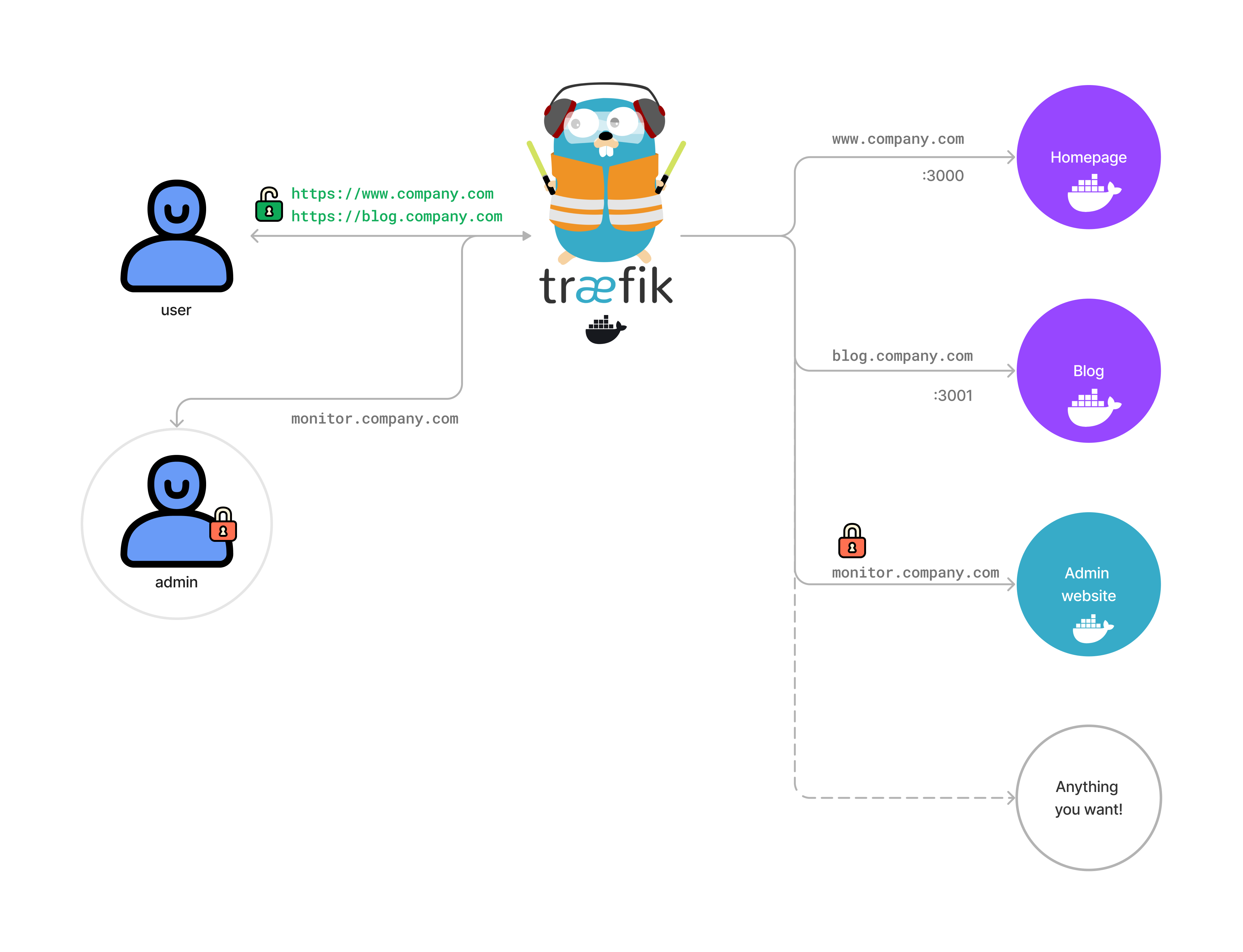
We will be building a small microservices architecture on our server using docker.
It looks like this:
Why
So that we can quickly deploy backend api using any language. It's fun to try out new languages and frameworks e.g Deno, Rust and maybe some Go lang in the future. This way we will be able to deploy the code and have live URL's to test with.
How
We will be using docker, docker compose and Traefik as the proxy to containers.
I have already set up a repo with different "services" here.
It includes:
- one folder per service, each service has it's own Dockerfile
- a single
docker-composefile to start the services from the root. - traefik.toml
- traefik_dynamic.toml
Traefik
Traefik is an open-source Edge Router that makes publishing your services a fun and easy experience. It receives requests on behalf of your system and finds out which components are responsible for handling them. source: Traefik
Imagine you have a website at www.website.com and an api at api.website.com, Traefik will direct the request to the appropriate service based on the sub domain.
Traefik will also help create SSL certificates using ACME provider Lets Encrypt.
This is configured via a .toml configuration file called traefik.toml and traefik_dynamic.toml. In these configuration files we specify:
- Entry points,
- Routers
- Middlewares, e.g SSL certificate resolver.
- Services Traefik supports
traefik.toml
Read file here
# EntryPoints # Network entry points into Traefik, defines which port will get accept traffick on either TCP or UDP [entryPoints] [entryPoints.web] address = ":80" [entryPoints.web.http.redirections.entryPoint] to = "websecure" scheme = "https" [entryPoints.websecure] address = ":443" # Enables the monitoring dashboard, a docker container itself, it shows you an overview of all your running containers (services) [api] dashboard = true # Certificate resolver, tells Traefik which certificate generator to use and configures the admin email. [certificatesResolvers.lets-encrypt.acme] email = "mannuel@themwebs.me" storage = "acme.json" [certificatesResolvers.lets-encrypt.acme.tlsChallenge] # specifies which provider you are using, there are a few supported ones (Kubernetes, Marathon, Rancher) [providers.docker] watch = true network = "web" # imports an extension configuration file for more traefik settings [providers.file] filename = "traefik_dynamic.toml"
traefik_dynamic.toml
Read file here
# Here we configure Middleware and HTTP Routers # Middleware are plugins that enable and can extend the features of Traefik # We are using the basicAuth on here to allow us to protect our admin portal website that shows our running containters # users: tells it which are the authenticated users. [http.middlewares.simpleAuth.basicAuth] users = [ "admin:$apr1$futE7qd5$CWn820MIlYZm4RILGBlB0/" ] # Router configuration # Rule: which url must Traefik must assign to the container that runs the web portal site, so entering https://monitor.company.com will load the admin site. # entrypoint: the name of middleware to use which is simpleAuth # service: which service is it, it is "api" and it is an internal one # certResolver: tells Traefik to use lets-encrypt as the provider. [http.routers.api] rule = "Host(`monitor.company.com`)" entrypoints = ["websecure"] middlewares = ["simpleAuth"] service = "api@internal" [http.routers.api.tls] certResolver = "lets-encrypt"
Admin page running on monitor.company.com domain, secured behind a username and password
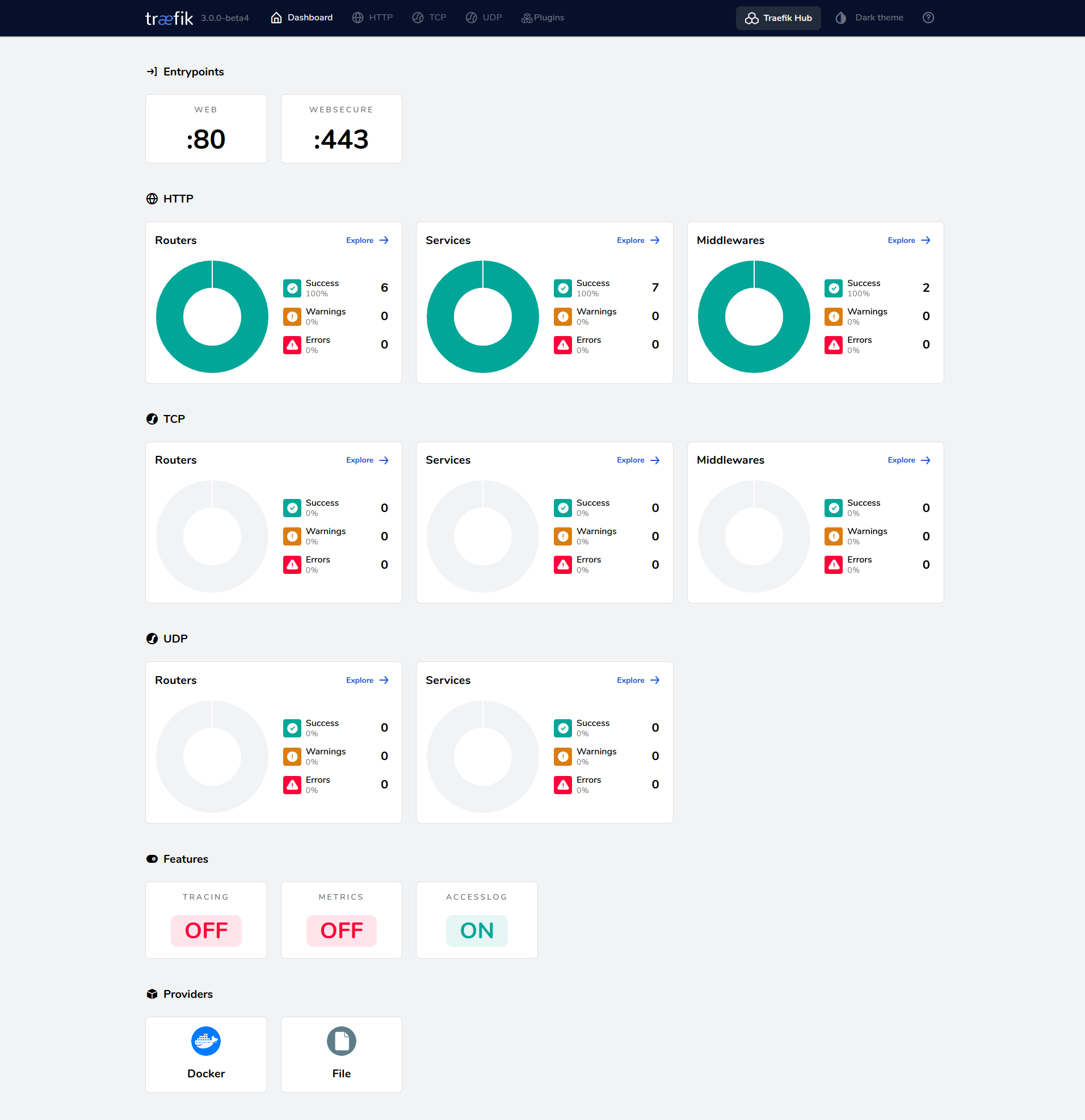
SimpleAuth middleware
Here is sample of my server showing the containers running on their respective ports
CONTAINER ID IMAGE COMMAND CREATED STATUS PORTS NAMES a153cafbc934 factbookapi "flask run --host 0.…" 2 weeks ago Up 2 weeks 5000/tcp factbookapi-service 9a32240c2384 musicwall "docker-entrypoint.s…" 2 weeks ago Up 2 weeks 3000/tcp musicwall-service a4d4ad1cd697 home "/docker-entrypoint.…" 2 weeks ago Up 2 weeks 80/tcp home-service 1346eb22b039 traefik:v3.0 "/entrypoint.sh --ac…" 2 weeks ago Up 2 weeks 0.0.0.0:80->80/tcp, :::80->80/tcp, 0.0.0.0:443->443/tcp, :::443->443/tcp traefik
That will do for now, take a break and we will dive into the docker parts in part 2.
Stay up to date
Consider keeping up to date with software development and design by signing up to my newsletter.
I will only email you when I make a new post.